LOS ANGELES, CA – March 28: FBI Assistant Director in Charge of the Los Angeles Field Office … [+]
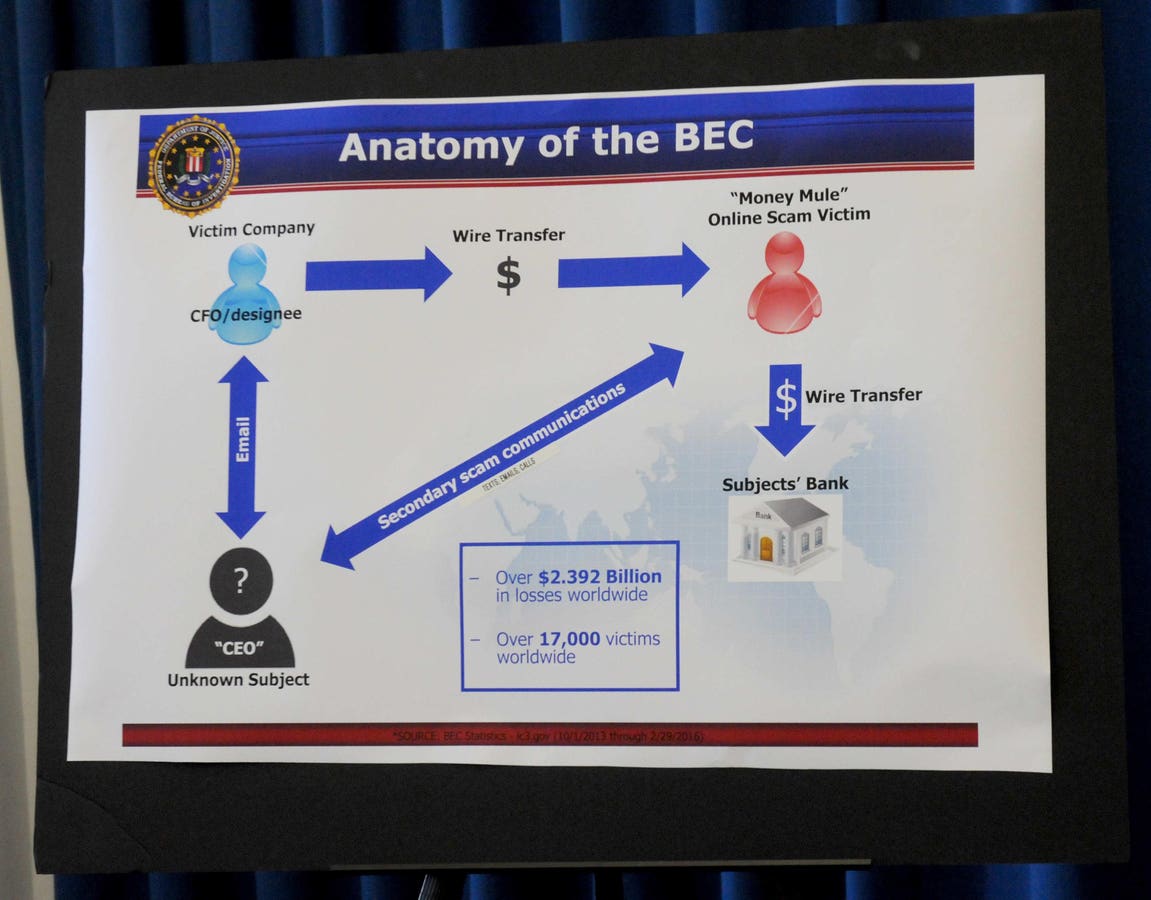
Business Email Compromise (BEC) is a scam perpetrated by fraudsters who, using social engineering tactics, pose as company executives or trusted vendors to lure employees at their target companies into transferring funds. to fraudsters. The FBI first started tracking (BEC) in 2013 and the scam has gotten bigger every year. The FBI reports that between October 2013 and December 2023 there were 305,033 domestic and international BEC incidents with associated losses of $55,499,915,582.
BEC is an equal opportunity scam targeting both small businesses and large corporations with incidents reported in every state and 186 countries.
How the scam works
Like many frauds and data breaches, BEC begins with a phishing or more specifically targeted phishing email created by the company to an employee of the target company that entices the employee to either download an attachment or click on a link that downloads malware that enables cybercriminals to infiltrate the target company’s computer networks. These initial emails to targeted company employees have become increasingly persuasive through the use of AI, which enables cybercriminals to gather information about who to target, as well as information to personalize the email and make it more persuasive. Once the target company’s computer networks are breached, cybercriminals are able to gather information to use to craft convincing emails that appear to be from a high-ranking company executive to an employee with the authority to transferred funds that direct the employee to the money link to an account that appears to be legitimate, but is actually controlled by cybercriminals. Often the email may come from the account of the CFO or other officer from whom the email appears to originate because the cybercriminal has managed to hack into and take over the high-ranking executive’s account. As part of the money laundering process, these funds often pass through banks in the United Kingdom, Hong Kong, China, Mexico and the United Arab Emirates.
New developments
Like all scams, BEC has evolved as technology has evolved and in one of the latest developments, instead of funds having to clear from bank to bank, the cybercriminal directs the funds to be transferred to a cryptocurrency escrow account where the funds are instantly converted into hard-to-follow cryptocurrencies.
In another AI-related evolution of BEC, deep forgery and voice cloning technology is being used to perform the trick. In 2019 the Wall Street Journal reported the first BEC incident of its kind where the CEO of a UK energy firm transferred $243,000 in response to a phone call in which he thought he was speaking to the CEO of his company’s German parent company .
A year later, as reported in Forbes, a voice cloning technology was again used to convince a branch manager of a Japanese company to wire $35 million to BEC fraudsters.
Judging by the increased number of BEC incidents, it appears that many companies are not taking the necessary steps to protect themselves from this crime even though the protocols that companies should put in place are not particularly costly, such as establishing an approval process for transactions that would require two or more principals to sign large wire transfers; using multiple means of communication to verify requested bank transfers and phone confirmation for bank transfer requests coming through emails and email confirmation for bank transfer requests coming by phone.
Finally, one of the best things that all companies should do to protect themselves from all types of fraud and cybercrime is to increase the education of their employees on how social engineering works to learn how to recognize it. him and do not fall victim to him.